Business Integration Solutions Documentation
Security Profiles
Security Profiles is a group of permissions to connect to an external service which contains settings depending on the authentication method/interface.
The security profile permissions in BIS allow users access to perform specific tasks in BIS.
The following permission sets are available.
- TI-BIS-ESSENTIAL
- TI-BIS-USER
- TI-BIS-ADMIN
for more information please refer Permission sets for BIS
The Account and the type of authentication method are stored in these profiles.
- BIS Users: can view and use security profiles, but cannot access their setup.
- BIS Admins: can view, create & setup security profiles.
Manage
Create a Security Profile
Creating a security profile enables users to connect to an external system.
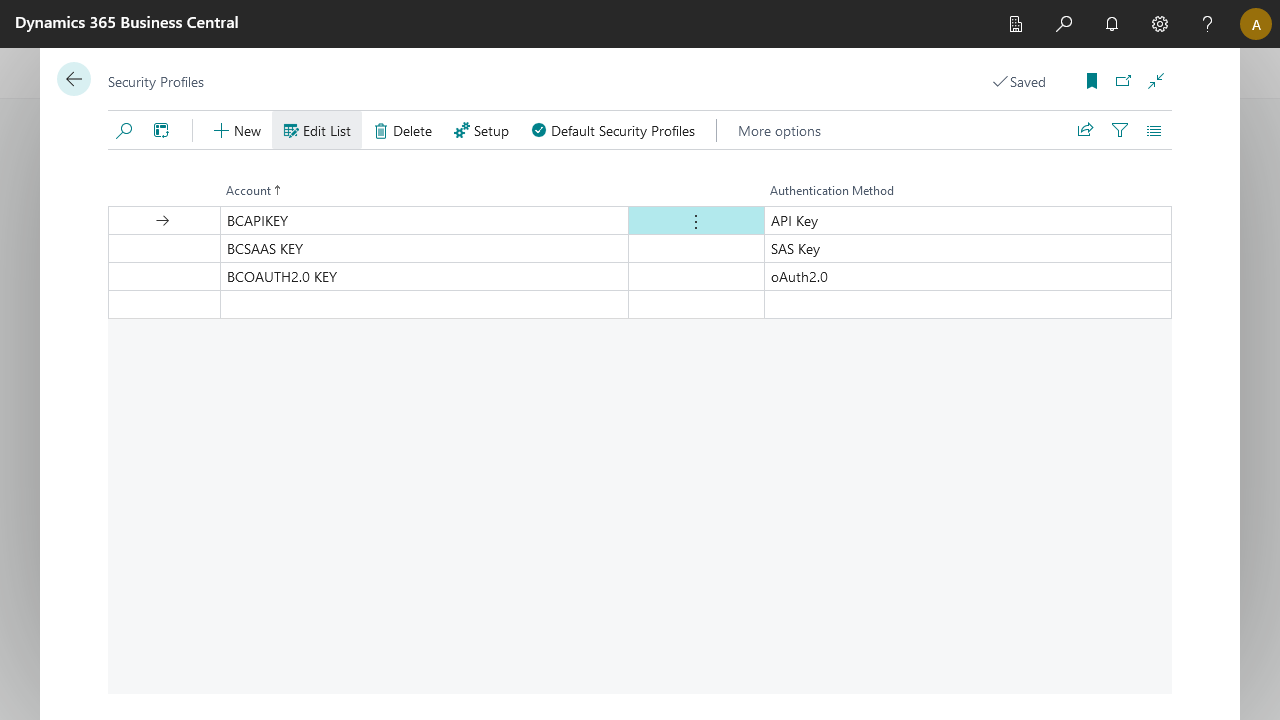
Account The account name. An identifier which BIS users and admins can use to identify the correct profile.
Authentication Method 4 Authentication methods can be used
Method Description SAS Key SAS Key authentication allows users to connect to external environment with limited access and permissions. API Key API Key authentication allows users to connect to external systems supporting api key authentication. Basic Auth Basic authentication with a username/password OAuth 2.0 OAuth 2.0 authentication allows users to connect to external systems supporting oauth 2.0 authentication.
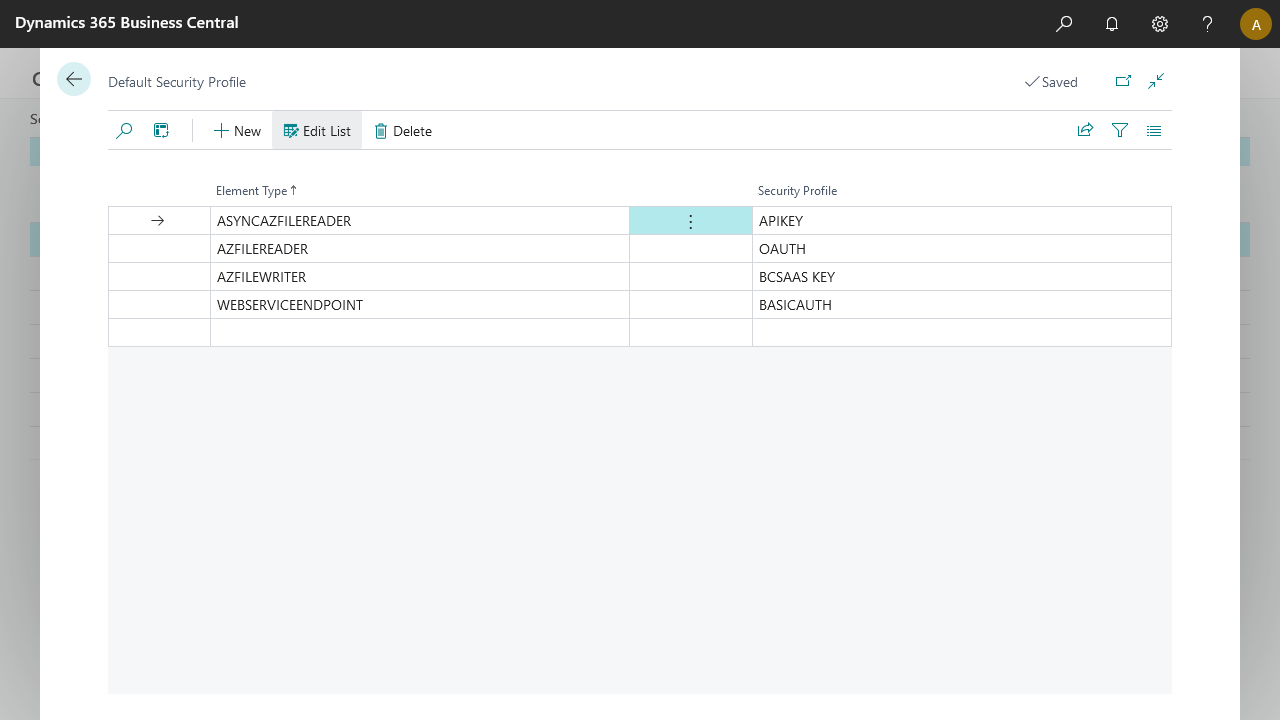
Default Security Profiles
Default security profiles are applicable for all supported End points.
User can assign one security profile per endpoint.
 .
.
Deafult security profile is automatically updated when we select respective endpoint.
please refer to
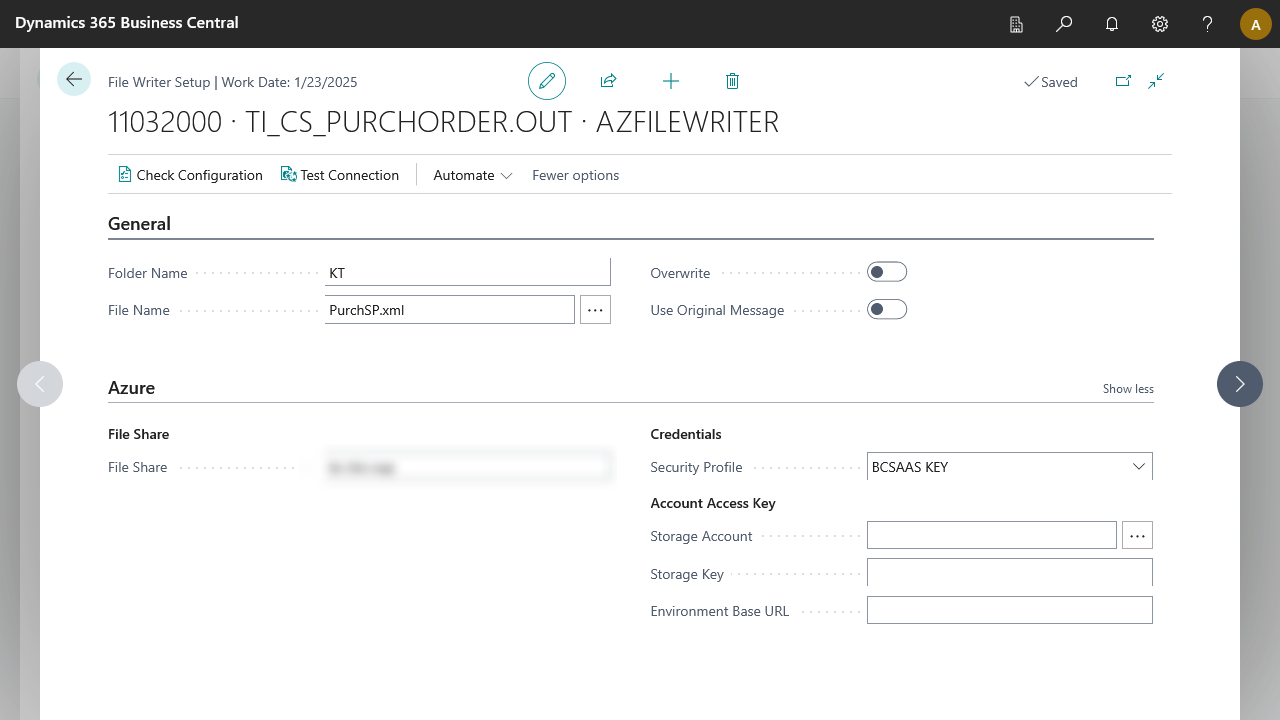
Default security profiles can be applied when importing configurations without existing security profiles
